READ TIME: 3 MIN

Data Security Using Collaboration Technology Starts Here
Our Product Management Team is tasked with instituting positive change and promoting efficiency across the organization and for NexusTek’s customer base. This can include the development of new products, to innovating how we deliver services to enable NexusTek’s staff to share information easily and reach higher levels of performance in their respective roles.
Collaboration across our organization is instrumental to the success of the Product Management Team and is a key factor in building a customer-centric culture. With offices in seven cities, it’s rare for all team members to be in the same room. This is where leveraging secure collaborative technology is key.
For a visual of how the integrated applications work for the Product Management team, below is a diagram representing our communication loops:
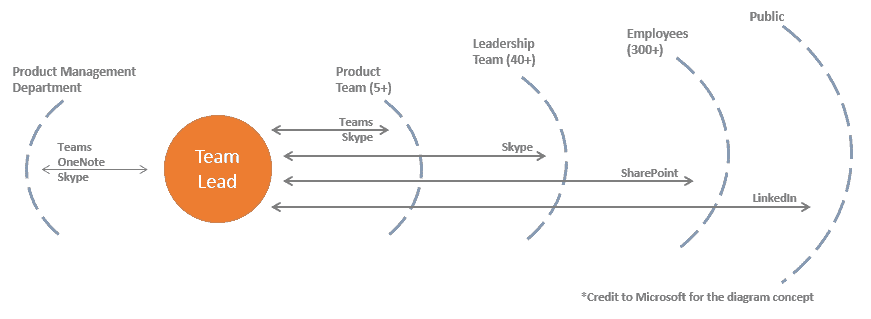
Outlook for email is still a primary tool used across these loops. However, you’ll see that the Office 365 Suite and especially Microsoft Teams, a component within Office 365, is taking over the typical email channels. Microsoft is investing heavily in Teams, due to the increased adoption of the many communication elements and collaborative features of the Office 365 Suite.
How can we validate the protection of our data?
The data we create in Outlook, Teams, Skype, OneNote, SharePoint, other cloud platforms, on our computers and our file servers is critical to our business as a managed IT services provider and increasingly for our customers.
For the SMB market, we need to ensure data security. This is why we are currently offering a bite-sized Microsoft 365 Security Assessment that includes a security score report for customers coupled with an actionable plan for remediation of issues uncovered in the assessment.
It is a valuable return for your investment of $495. Request your Microsoft 365 Security Assessment from a qualified NexusTek engineer today!
Visibility into Possible Security Gaps in Your Environment
Many clients who have opted to invest in this security assessment, have also made the decision to follow through with engineer remediation report based on the results. Specifically, companies with compliance requirements have found that having a NexusTek engineer analyze the findings and follow up with an action report, proved to streamline decision-making where securing gaps in their environment were a concerned.
Just one example of a common security audit remediation project would be adding email security with Office 365 Advanced Threat Protection that includes planning, configuration and testing.
Get visibility to your environment and close the security gaps that is putting your business at risk.






