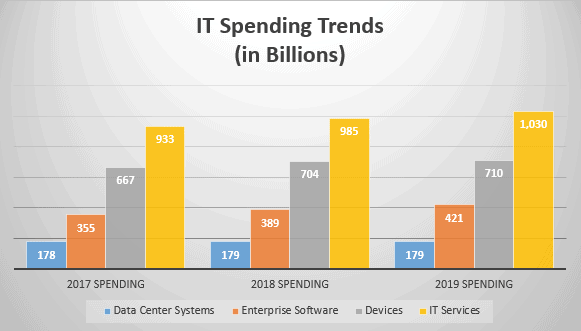
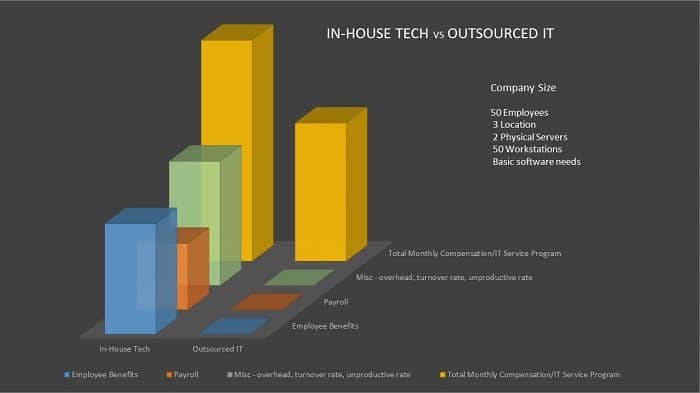
READ TIME: 3 MIN

3 Things to Know When Updating Your Phone System
Lower Your Cost of Ownership
Modern communications have certainly evolved well beyond the vision of our forefathers. When we reflect on the number of touchpoints we now manage between employees and customers, it is no wonder the pace of business growth is at an all-time high. Whether it’s email, chat, messaging apps, or video conferences, you need open communication to run your business. So, as you’re comparing phone systems and unified communications platforms, here are some things you’ll want to consider.
Right Plan, Right Person
When calculating the cost of a new phone system, you’ll want to factor in “add ons” to get the features and capabilities that will best serve your business goals. One of the advantages of working with NexusTek is our ability to tailor your Unified Communications System to your business needs, so each employee has the service level they need based on their daily workflow. If you require that your management team has access to deeper analytics and monitoring capabilities, but you only need basic functionality for the rest of your staff or call center, you can lower your total cost of ownership by picking the right plan for each person.
Minimizing Business Risk
Most business owners agree that risk is a scary word. You might take risks on marketing a new product but when it comes to your phone system, taking risks is like driving without insurance. By partnering with NexusTek, we’ll help you reduce your risk by controlling all communications on our platform end-to-end. Your customers’ data stays secure while you stay compliant – making it a “win-win” for your business and your customer!
Grow the Right Way
Growth can be another scary proposition for business owners. From big decision like moving into new markets, opening new offices, or acquiring new businesses, ensuring that your operational standards are maintained across your organization is a requirement.
Let NexusTek worry about setting up your communications system and adhering to regulatory environments. At the end of the day, our service is more than just phone coverage. NexusTek can help you comply with local telecommunications rules, set up your offices with local numbers and provide an interface that your employees’ can feel comfortable with using from the start.
When choosing a Unified Communications partner, it’s critical to dive into the technology, business relationships, and support capabilities of each provider you consider. NexusTek listens to your own specific communications needs to ensure your new phone system exceeds your expectations. Contact us about NexusTek’s Unified Communications program to learn more.